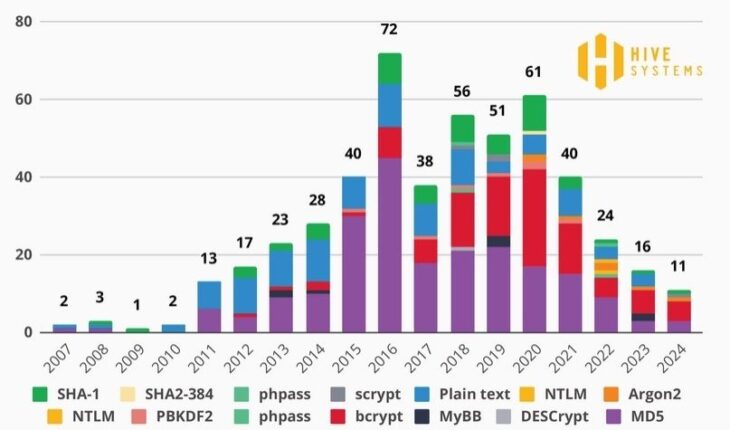
Hive Systems, which specializes in cybersecurity, has been testing password cracking using brute-force attacks for several years. All this time, the object of research was passwords encrypted using the widely used MD5 algorithm, the hashes of which in many cases are easy to “break through”.
However, organizations are increasingly turning to more secure algorithms, such as Bcrypt, which has become the most popular in recent years.
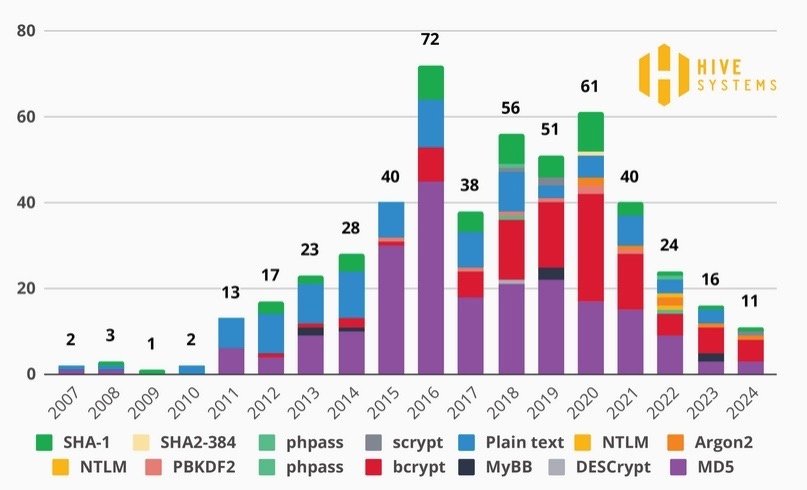
That’s why Hive decided to shift the focus and try Bcrypt password hashes by heart, using a dozen NVIDIA GeForce RTX 4090 GPUs.
Research has shown that passwords that are 7 characters long and shorter can be cracked within a few hours. These results are noticeably different, because in last year’s tests, weak passwords of 11 characters encrypted with MD5 were cracked instantly. The same 11-character password can be cracked in 10 hours using the Bcrypt algorithm.
The company claims that strong passwords (containing numbers, uppercase and lowercase letters, symbols) and relatively strong passwords (containing uppercase and lowercase letters) are quite difficult to crack if they are longer than eight characters. These Bcrypt-protected passwords can take months or years to crack.
In the course of the study, experts received a hash associated with a randomly generated password and tried to crack it. Hive noted that passwords generated in a non-random way are cracked much easier and faster, since people are quite predictable.